🏷️ Tech Stack: Palo Alto Networks • Panorama • IPS/IDS • SSL/TLS Decryption • CVE Monitoring • DoS Protection • EDL • VMware ESXi • Centreon
Methodologies: Enterprise Security Operations • Network Architecture • Threat Intelligence • Risk Management
My Role: Junior engineer responsible for IPS/IDS module deployment, optimization, and operational procedures documentation
Production Enterprise Project - Apprenticeship at Orange Reunion IP Network Infrastructure | 2024-2025
📋 TL;DR - Executive Summary
Context: Deployed and optimized Advanced Threat Prevention IPS/IDS module on newly migrated Palo Alto NGFW protecting critical services network.
Challenge: Configure enterprise-grade perimeter security with SSL/TLS decryption, CVE vulnerability monitoring, DoS protection, and threat intelligence integration while maintaining service availability for critical infrastructure.
Solution: Structured 5-phase deployment (Research & Planning → Pre-production → Production → Optimization → Documentation)
Results: 40% reduction in medium-severity international threats, partly automated malicious IP blocking, multi-layer protection deployment, and complete knowledge transfer documentation enabling team operational autonomy.
Impact: Secured critical Internet gateway for large network infrastructure.
🏢 Apprenticeship Context:
My Apprenticeship took place within the IP Networks department of Orange Réunion (DTRM), responsible for designing, deploying, and securing the operator’s critical network infrastructure.
Strategic Migration to Palo Alto Networks
The IP Networks department had just completed a strategic migration of its security equipment to Palo Alto Networks firewalls, a solution offering advanced threat detection and prevention capabilities.
Cyberthreat Evolution
This migration addresses a security context characterized by:
- Increasing sophistication of attacks with elaborate evasion techniques
- Explosion of DoS/DDoS attacks targeting critical telecommunications infrastructure
- Multiplication of vulnerabilities in perimetric security equipments
- Emergence of IoT threats and botnet expansion
Role of NGFW in Defense Strategy
The Palo Alto firewalls constitute the first line of defense for Orange Réunion’s web services, ensuring:
- Intelligent filtering of Internet ↔ internal network traffic
- Real-time detection of suspicious behaviors
- Proactive blocking of intrusion attempts before impact on internal systems
🛠️ Palo Alto Networks & Associated Tools Overview
Palo Alto Networks is a global leader in cybersecurity, recognized for its Next-Generation Firewall (NGFW) solutions. Unlike traditional firewalls that are limited to port and protocol filtering, Palo Alto solutions integrate advanced features such as:
Components Deployed at Orange Réunion
In the Orange Réunion environment, two main components of the Palo Alto solution have been deployed:
1. VM-Series Virtual Firewalls
Deployed on VMware ESXi infrastructure, these virtual firewalls offer the same functionality as their physical equivalents.
2. Panorama - Centralized Management Interface
This centralized management platform enables administration of all Palo Alto firewalls from a single interface, providing:
- Centralized security rule configuration with simultaneous deployment
- Real-time monitoring of network activity and threats
- Consolidated reporting and centralized log analysis
 Panorama Web Interface - Centralized Management Overview
Panorama Web Interface - Centralized Management Overview
🎯 Core Challenge and Primary Mission
How to optimize cybersecurity operations management in an evolving threat landscape?
Central Challenge: How can we optimize the management and automation of network security operations to effectively counter the constantly evolving cyberthreat landscape?
This challenge encompasses several critical questions:
- How can we efficiently configure Palo Alto firewalls to maximize network protection capabilities?
- How can we fully leverage the intrusion detection and prevention module’s advanced features?
- How can we automate recurring operational tasks to improve overall security efficiency?
- How can we establish comprehensive documentation to ensure long-term solution sustainability?
To address these challenges, my primary mission focused on configuring, operating, and automating the IPS/IDS module of Palo Alto firewalls.
📅 Daily Operations and Operational Responsibilities
Beyond the primary IPS/IDS project, I managed various operational responsibilities ensuring continuous service availability of the Palo Alto infrastructure:
- Security Log Monitoring and Analysis
- Blocking List Decision Management
- SSL/TLS Certificate Management
- PAN-OS Equipment Updates
- Security Rule Management
- Documentation and Communication
🏗️ Infrastructure Architecture & Enterprise Context
Technical Architecture and Solution Design
Palo Alto firewalls are positioned as Internet gateway protection to secure internal web services and critical network infrastructure.
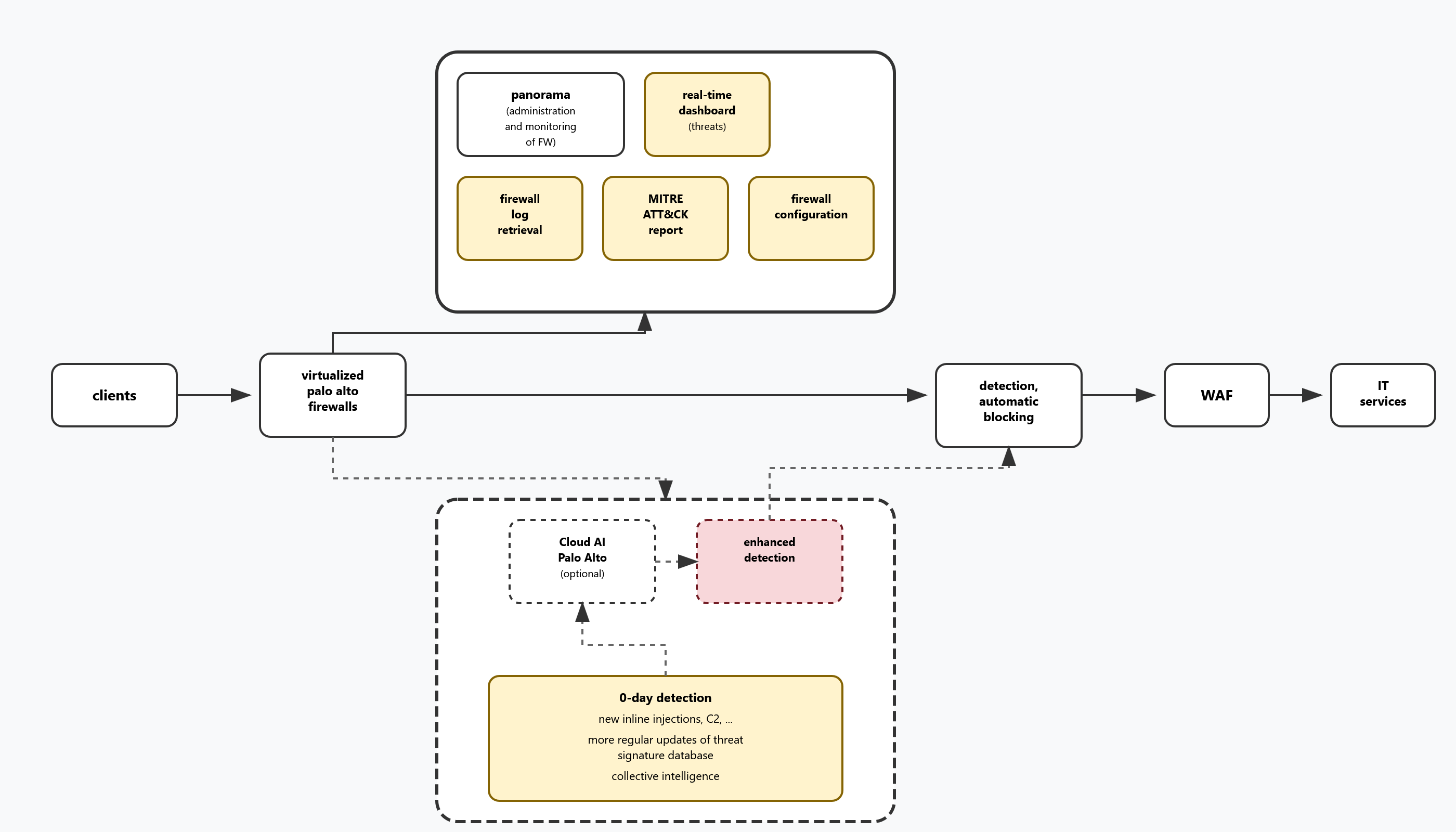 Simplified Architecture - Palo Alto Firewalls and Panorama Positioning
Simplified Architecture - Palo Alto Firewalls and Panorama Positioning
Multi-Vendor Ecosystem Discovery
The infrastructure operates within a complex multi-vendor ecosystem segmented across different security zones—specific details are omitted for confidentiality requirements.
This architectural complexity demands comprehensive understanding of traffic flows and system interactions for effective troubleshooting and service deployment.
Virtualized Infrastructure and High Availability
Deployed Palo Alto Components:
- VM-Series Firewalls: Deployed on VMware ESXi infrastructure in active/passive high-availability pairs
- Virtualized Panorama: Centralized management platform for comprehensive firewall orchestration
- VMware Architecture: VM mobility capabilities enabling zero-downtime maintenance operations
Integration with Centreon/Panorama Monitoring
Multi-Layer Monitoring Strategy:
- Centreon: Infrastructure monitoring (availability, performance metrics, alert thresholds)
- Panorama: Palo Alto-specific monitoring (threat detection, session analytics, throughput analysis)
- VMware vSphere: Virtualized resource monitoring (CPU utilization, memory allocation, storage performance)
This virtualized architecture ensures flexibility, resilience, and scalability for mission-critical telecommunications infrastructure operations.
🛡️ IPS/IDS Module: Core Mission
Traditional vs. Advanced Filtering
Traditional firewalls are limited to basic port/IP/protocol filtering, becoming insufficient against modern threats using legitimate ports (443, 80) and encrypted traffic.
Palo Alto NGFWs enable advanced capabilities through SSL/TLS decryption and application-layer analysis:
- Application-specific control (YouTube, Slack, Teams) beyond port-based filtering
- Real-time threat intelligence with dynamic blacklists and malware detection
- Proactive CVE protection with daily signature updates and behavioral analysis
- Automated response from alerting to IP blocking and session termination
Strategic Advantages:
- Advanced threat detection identifying sophisticated attacks
- Proactive protection blocking exploits before they reach targets
- Deep visibility into attack techniques and threat actor methodologies
- Operational efficiency through automated responses to common threats
🛡️ Vulnerability Monitoring Configuration
Vulnerability Monitoring and Supervision Architecture
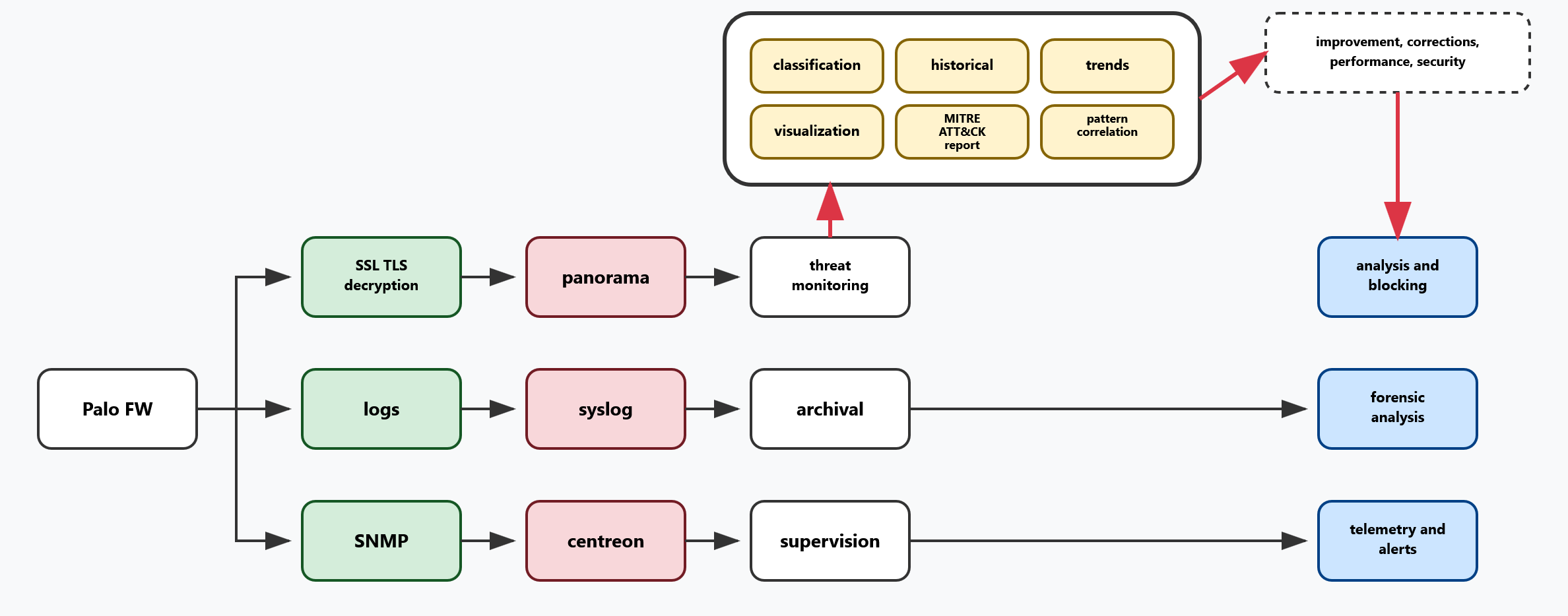 Vulnerability Monitoring Architecture - Processing Flows and Supervision Framework
Vulnerability Monitoring Architecture - Processing Flows and Supervision Framework
The Palo Alto firewall generates three distinct data flows for comprehensive monitoring:
- SSL/TLS decryption → Real-time threat analysis via Panorama
- Security logs → Long-term storage and forensic analysis via syslog
- SNMP metrics → Infrastructure monitoring via Centreon
The system centralizes six analytical capabilities and generates three output categories for continuous security improvement, ensuring complete threat visibility and graduated response mechanisms.
SSL/TLS Traffic Decryption
To analyze encrypted traffic, SSL/TLS decryption configuration is essential. This forms the foundation of packet analysis for this type of IPS/IDS system.
Technical Analogy: The Safe Principle
💡 Technical Metaphor: Imagine a safe being sent from a client to our services. The client and destination service have agreed upon a password. We, at the IPS/IDS module level, know this password.
When the safe arrives at our gateway, before allowing it entry, we open it (decryption), inspect its contents, and if nothing dangerous is detected, we close it and allow passage. Otherwise, we block it immediately.
This real-time deep packet inspection capability constitutes the major advantage of Palo Alto NGFWs.
Competitive Advantage vs Alternative Solutions
The Palo Alto module distinguishes itself through pre-connection inspection capabilities:
- Suricata: Limited inspection without comprehensive decryption
- CrowdSec: Post-exploitation analysis via log correlation
- Palo Alto IPS/IDS: Real-time inspection of decrypted traffic before it reaches its target
SSL/TLS Traffic Decryption Implementation
Decryption Configuration Process
The process is structured in 5 steps for SSL/TLS decryption configuration:
⚠️ Performance Consideration: Since Palo Alto equipment is dimensioned for very large-scale infrastructures, decryption of moderate traffic volumes causes minimal to no noticeable performance impact. Performance testing remains recommended for validation.
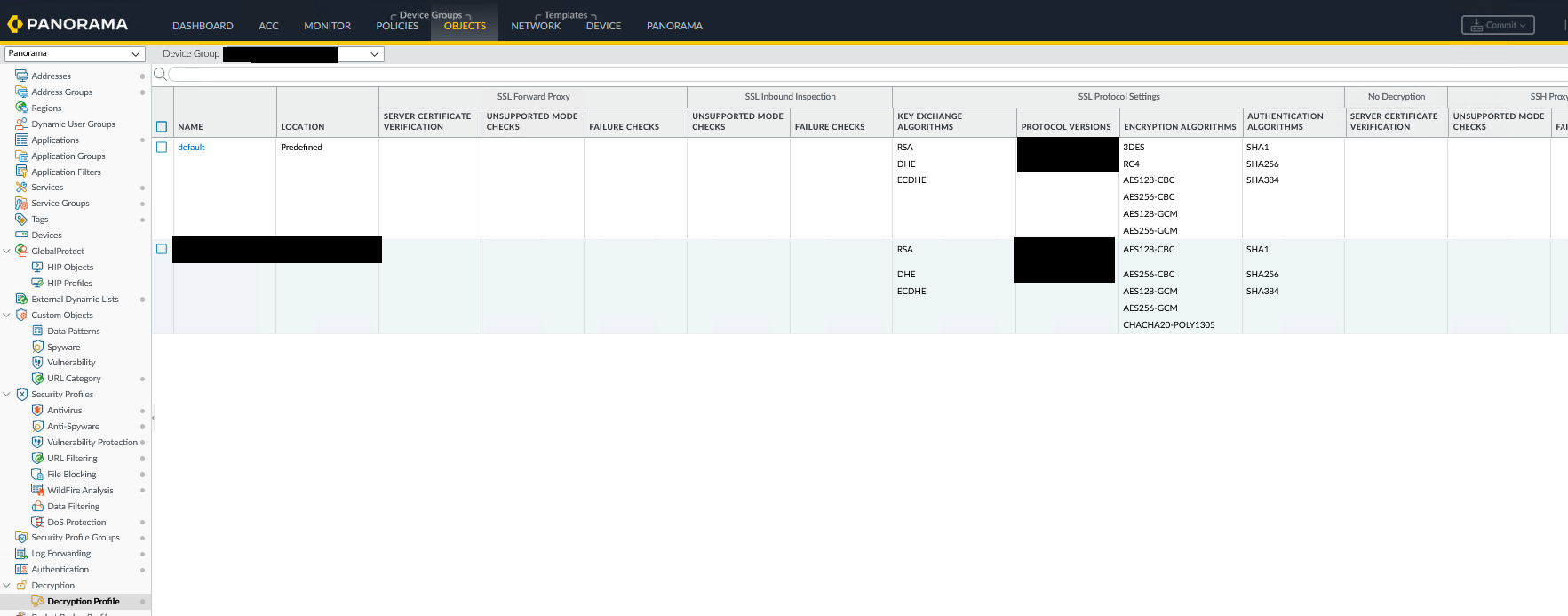 Decryption Profile Configuration List
Decryption Profile Configuration List
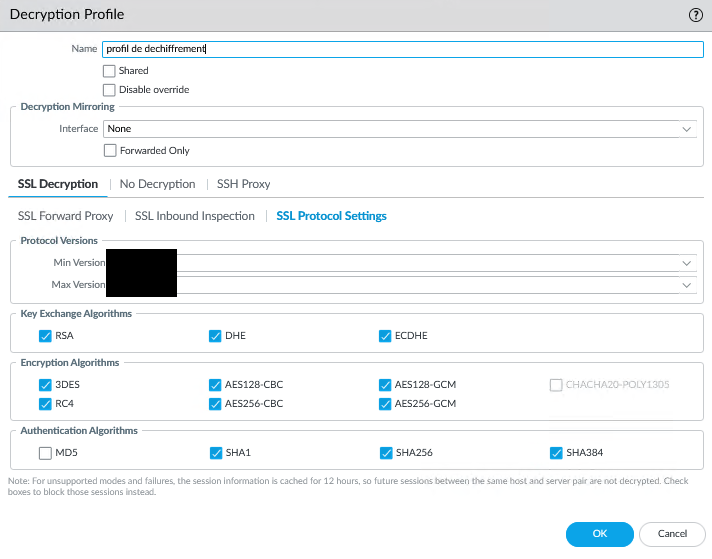 Decryption Profile Configuration - Supported Encryption Algorithms
Decryption Profile Configuration - Supported Encryption Algorithms
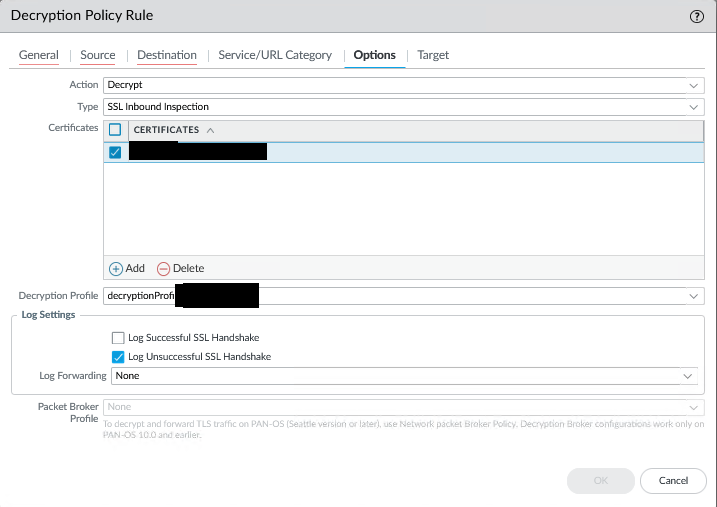 Decryption Rule Configuration - Associated Certificate
Decryption Rule Configuration - Associated Certificate
As shown in the capture below, the flow is not decrypted as it displays SSL (indicating only the encryption protocol).
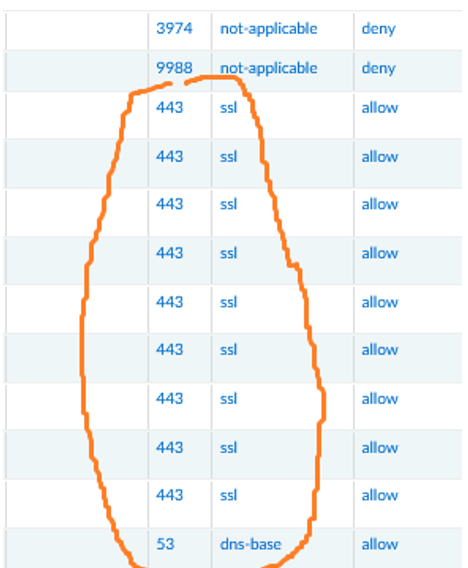 Example of Non-Decrypted Flow
Example of Non-Decrypted Flow
When the flow is decrypted, we can see the application type used for the exchange (such as web-browsing below).
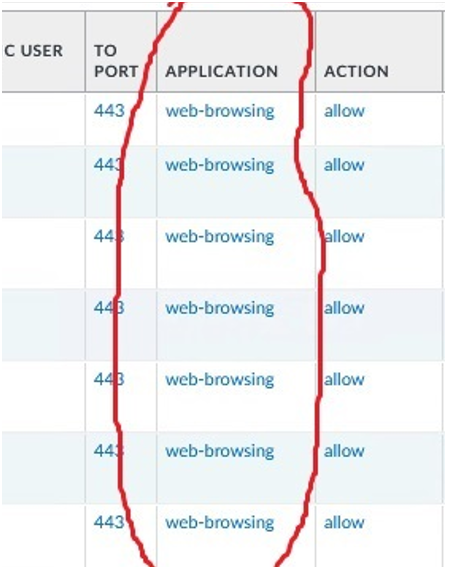 Example of Decrypted Flow
Example of Decrypted Flow
CVE Protection Profiles
Following decryption configuration, creating vulnerability protection profiles is essential. Tailored to each enterprise IT requirements, these profiles define monitored and non-monitored vulnerabilities, along with automated firewall actions in case of exploitation attempts.
These profiles leverage vulnerability databases (CVE) that Palo Alto updates daily. I configured automatic database updates through the Panorama GUI.
CVE Profile Characteristics
- Definition of monitored and non-monitored vulnerabilities with selective coverage
- Hierarchical threat classification (Critical, High, Medium, Low) provided by Palo Alto
- Granular firewall actions based on exploitation attempts and CVE severity levels
As an example, when a profile monitors Windows CVEs, decrypted traffic is compared against Palo Alto’s signature database to identify vulnerabilities targeting Windows systems present in the infrastructure.
Severity Hierarchy and Actions (alert/block/reset)
Configuring specific actions to trigger when these threats are detected is crucial. We can therefore define severity-based actions according to Orange Réunion’s security strategy.
Example: A critical severity CVE is blocked for X hours. An informational CVE connection is allowed.
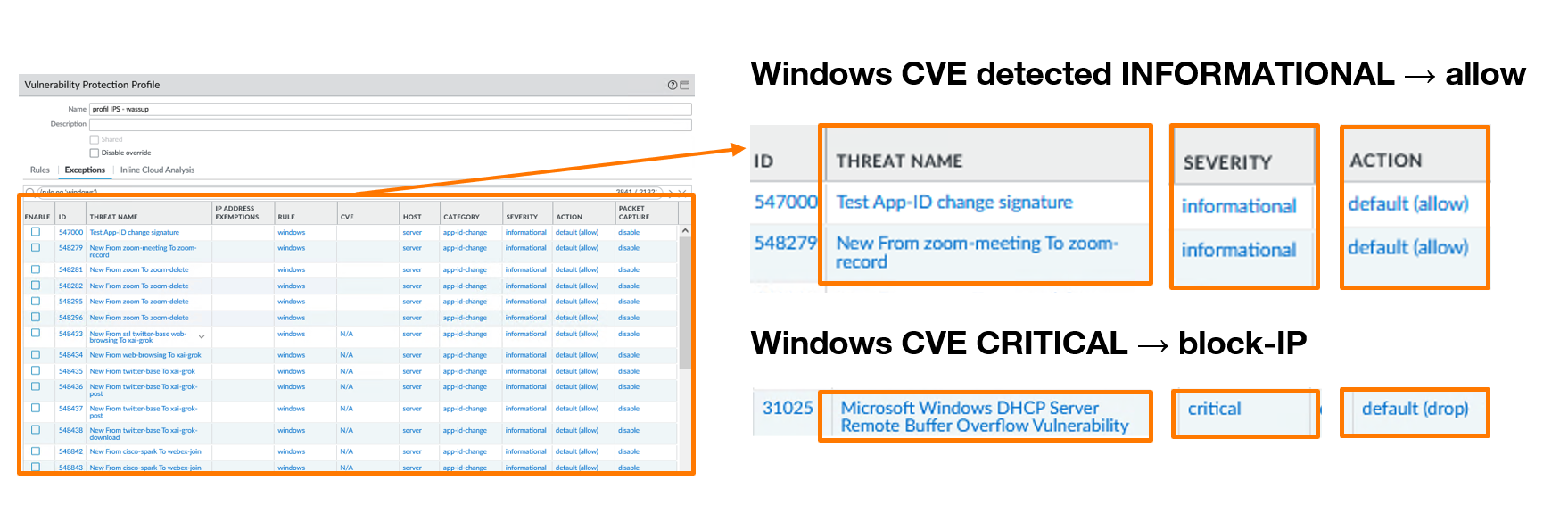 Windows CVE List Classified by Palo Alto with Configured Actions
Windows CVE List Classified by Palo Alto with Configured Actions
I configured four rules corresponding to our graduated response strategy:
# CVE Protection Profile Configuration
cve_protection_rules:
rule_1_critical:
severity: "Critical"
action: "Block-IP"
logic: "Systematic blocking"
rule_2_high:
severity: "High"
action: "Block-IP"
logic: "Systematic blocking"
rule_3_conditional:
severity: ["Medium", "Low"]
action: "Alert"
condition: "If system/service present"
rule_4_global:
severity: "All remaining CVEs"
action: "Alert"
position: "Last resort"
This approach enables proportionate response: strict actions for Palo Alto-classified critical vulnerabilities, targeted monitoring for others based on our specific requirements.
Security Rule Application
After configuration, the CVE protection profile is applied to specific traffic flows on the firewall. Packets from this flow are decrypted then analyzed against the CVE database, generating detailed threat logs for each detected exploitation attempt.
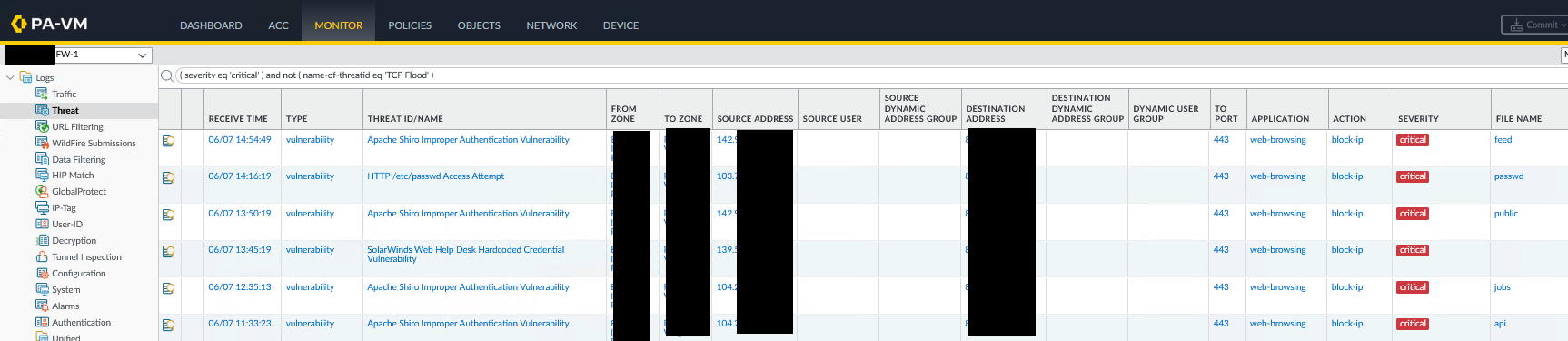 Extract of Detected and Filtered Threat Logs
Extract of Detected and Filtered Threat Logs
Log Analysis and Reporting
Temporary Blocking Limitations
Unlike SIEMs that analyze attacker behaviors over time, the Palo Alto IPS/IDS module does not provide precise behavioral reporting. It excels in real-time detection but presents a strategic limitation:
- Temporary blocking of malicious IPs (e.g., 4 hours)
- Potential return of attackers after expiration
- Behavioral adaptation: attackers understand thresholds and adjust their techniques
- Detection evasion by staying under detection radars
Need for Extended Behavioral Analysis
To counter these limitations, a comprehensive overview is essential:
- IP behavior over time (recurrence patterns, evolution)
- Targeted CVEs by specific attackers
- Attack paths and campaign duration
- Evasion patterns and adaptation techniques
This is why additional threat log analysis is crucial for effective security operations.
Analysis Evolution: Manual → Automated
Manual Analysis Process: I established a structured manual analysis workflow:
- Daily log extraction via Panorama
- Manual event correlation
- Recurring IP identification
- Exploited CVE analysis
But then I developed automation: Facing increasing alert volumes, I developed the ThreatDetectionTool to automate this behavioral analysis.
🔗 Learn More: Discover the ThreatDetectionTool in my dedicated post which details complete automation of threat behavioral analysis.
Reporting and Visualization
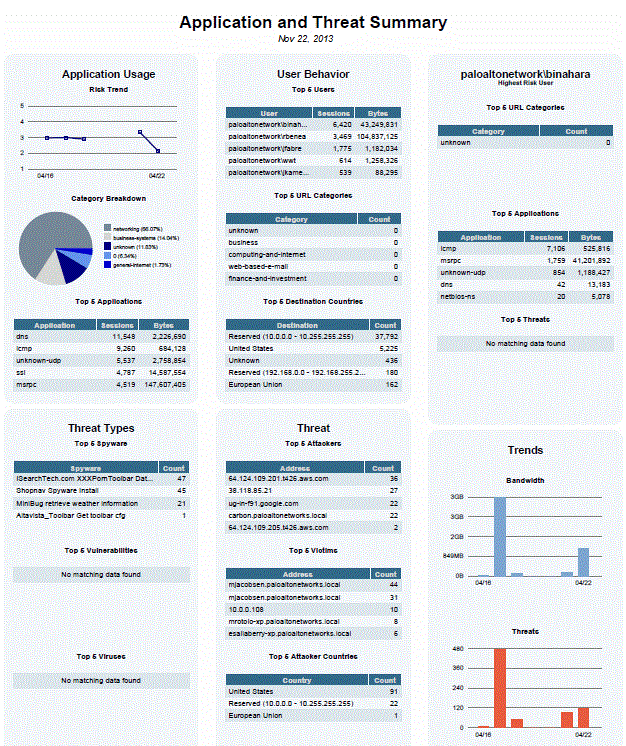
To exploit and present log data, I utilized:
Palo Firewall Integrated Visual Reports:
- Pre-configured charts
- Temporal trends and geographical analysis
Advanced Automation:
- Python analysis script I developed for detailed reporting
- Automatic generation of IP blocking lists and reports
 Geographic Threat Visualization - Attack Source Analysis
Geographic Threat Visualization - Attack Source Analysis
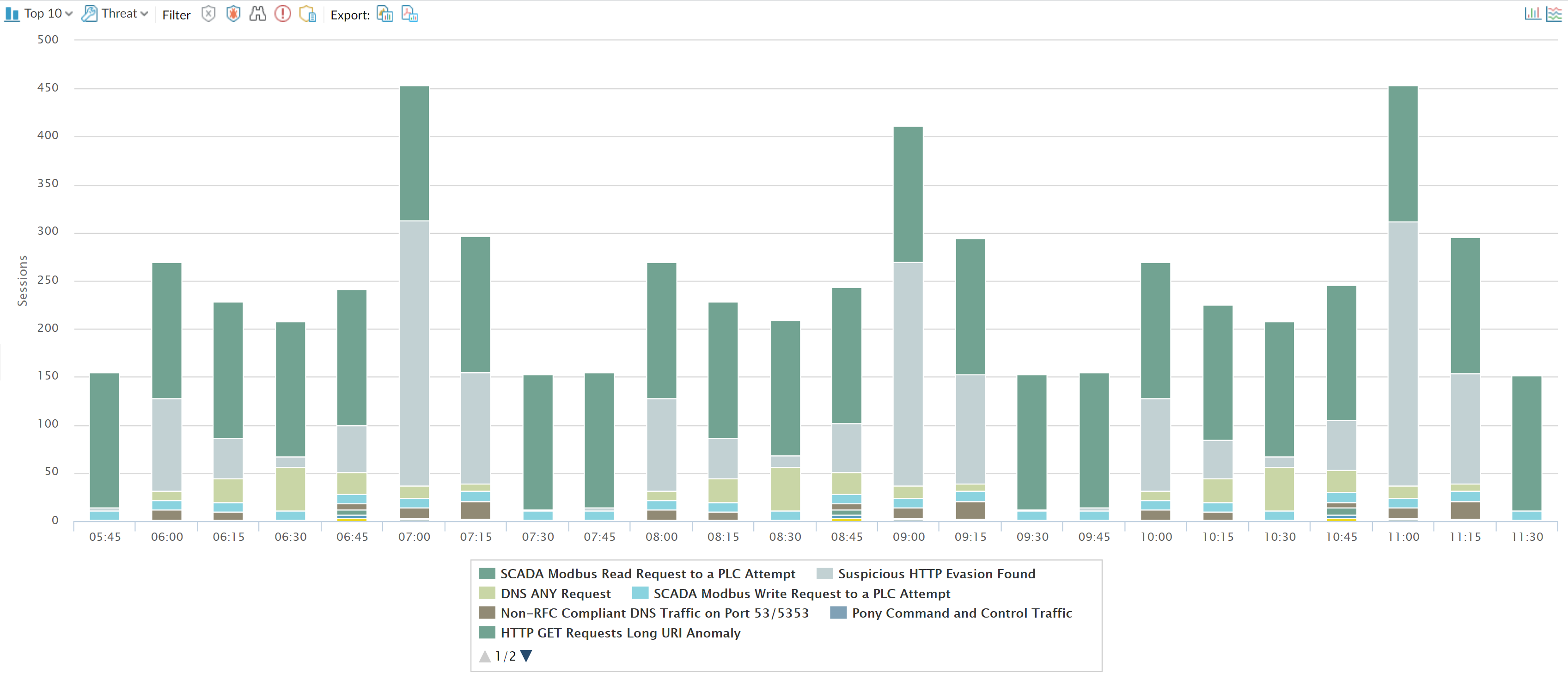 Application-Specific Threat Analysis Dashboard
Application-Specific Threat Analysis Dashboard
These reports facilitate strategic decision-making and enable effective communication with both technical and management teams.
⚡ DoS/DDoS Protection & BGP FlowSpec
What is a DoS/DDoS Attack?
A DoS attack (Denial of Service) aims to make a service unavailable by saturating it with requests. The objective is simple: overwhelm the server so it can no longer respond to legitimate users.
Common Attack Types:
- SYN Flood: Floods the server with unfinished TCP connection requests
- UDP Flood: Saturates bandwidth with massive UDP traffic
- ICMP Flood: Bombards with pings to consume system resources
The IPS/IDS module of Palo Alto firewalls features a protection option (limited but functional) against these attack vectors.
Configuration Logic: DoS Profile + DoS Rule
DoS protection is structured around two complementary components DoS rule and DoS Profile:
This separation allows reusing the same profile across multiple rules with different scopes and applications.
Protection Modes: AGGREGATE vs CLASSIFIED
A critical configuration choice in DoS protection is the difference between AGGREGATE and CLASSIFIED modes:
AGGREGATE Mode applies global thresholds to entire traffic within a zone, meaning that a 100 CPS threshold represents a total limit for all users accessing all services combined. While this approach provides broad protection, it presents a significant risk of global blocking during massive DDoS attacks, as legitimate users may be impacted when the collective threshold is exceeded. This mode is typically used as a second line of defense behind dedicated anti-DDoS equipment.
In contrast, CLASSIFIED Mode ✅ applies individual thresholds to each specific flow, where a 100 CPS threshold means that each user can establish 100 connections per second to each service independently. This approach provides precise detection capabilities without impacting legitimate users, as each flow is monitored separately rather than collectively.
Strategic Choice: CLASSIFIED Mode
I selected CLASSIFIED mode to optimize protection capabilities:
- Independent monitoring of each flow/user
- Customized thresholds (connections per second) per flow
- Targeted actions: blocking only the problematic flow/user
- Preservation of availability for legitimate users
This approach provides fine-grained and efficient security management while maintaining service availability for legitimate traffic.
DoS Profiles: Thresholds (SYN FLOOD, UDP, ICMP) and Blocking Duration
Configuring blocking thresholds requires a delicate balance between security and availability, along with comprehensive understanding of the IT infrastructure and its usage patterns. Access to traffic analysis tools is essential for optimization.
After observation and adjustment, I defined optimized thresholds for all protocols (example values):
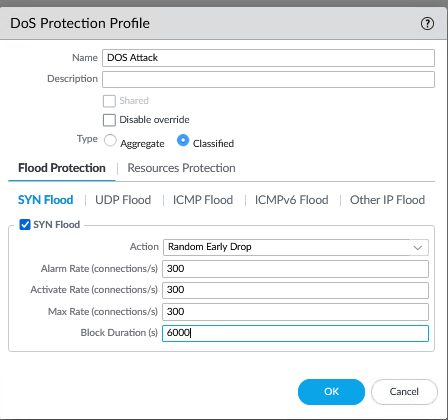 DoS Profile Configuration Extract (example values)
DoS Profile Configuration Extract (example values)
DoS Rule Creation
Creating a DoS rule involves defining:
- Source zone and addresses to include/exclude (partners, Orange services)
- Destination and concerned services (e.g., HTTPS)
- DoS profile to apply
- Actions upon detection
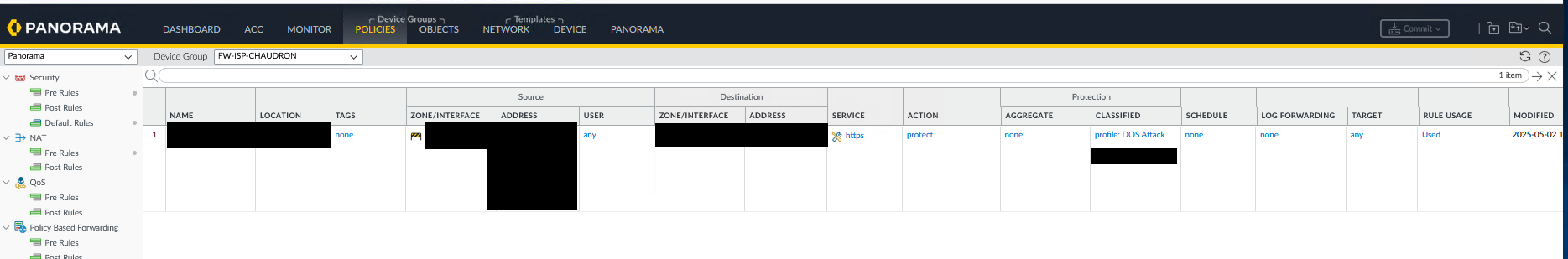 Configured DoS Protection Rules Extract
Configured DoS Protection Rules Extract
Analysis and Limitations: Toward BGP FlowSpec
The integrated anti-DoS/DDoS functionalities in Palo Alto firewalls do not constitute a first-line solution against these attacks. While they reduce exposure, they are typically preceded by:
- Load balancers for traffic distribution
- Dedicated proxies for application-layer filtering
- Specialized upstream anti-DDoS equipment
My research during the apprenticeship revealed that BGP FlowSpec represents one of the most effective protections against volumetric attacks. This solution is particularly suited to Orange Réunion’s context**.
BGP FlowSpec Operation
This protocol operates through an automatic propagation mechanism:
- Attack detection → Automatic BGP alert to upstream router
- Information propagation across all ingress/egress interfaces
- Inter-operator distribution to BGP FlowSpec-compatible routers
- Source-level blocking directly at the provider level
- Global propagation via BGP throughout the routing infrastructure
Advantages for Orange Réunion
- Upstream blocking before link saturation
- Automatic propagation within Orange France infrastructure
- Drastic reduction of malicious traffic reaching firewalls
- Scalability for significant volumetric attacks
Implementation Considerations
Technical Prerequisites:
- BGP FlowSpec-compatible routers in infrastructure
- Inter-operator agreements for inter-domain propagation
- Scrubbing center configuration for traffic redirection
Limitations:
- Effective for volumetric attacks, less so for sophisticated application-layer attacks
- Dependency on inter-operator agreements for global propagation
The BGP FlowSpec solution might constitute an evolution to strengthen protection against volumetric DDoS attacks, effectively complementing every DoS protections already configured.
📋 Built-in EDL Configuration and Usage
EDL Overview and Security Role
EDL are a powerful mechanism in Palo Alto firewalls that allow retrieval from external web servers of IP address lists, URLs, or objects for dynamic use in security rules as allow lists or block lists.
Major advantage: List updates without commit required - firewalls automatically query sources and apply changes in real-time.
Built-in EDL: Integrated Threat Intelligence
In the case of built-in EDL, Palo Alto Networks directly provides malicious IP address lists as part of the Advanced Threat Prevention license. These lists are integrated into the antivirus database updated daily (update need to be configured).
Their integration represents a significant improvement to our security posture at no additional cost.
Built-in EDL Configuration
Palo Alto Networks provides four main categories of built-in EDL:
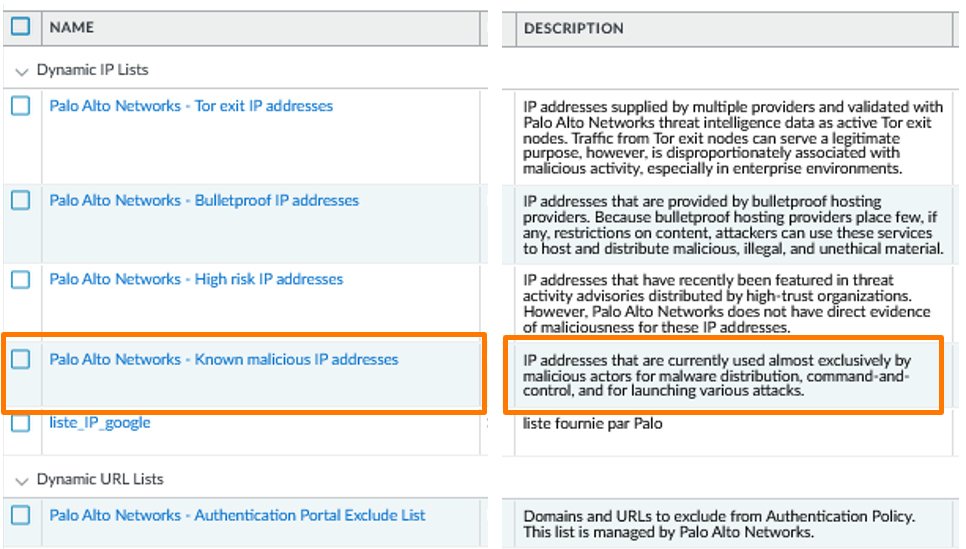 Palo Alto Built-in EDL List - Available Malicious IP Lists
Palo Alto Built-in EDL List - Available Malicious IP Lists
Strategic List Selection
After analysis, I determined that the first three categories were particularly relevant for our context and should be integrated as priority implementations.
Threat Intelligence Integration
Phase 1: Update Activation
- Activation of antivirus database updates (initially unused due to dedicated WAF for application layers)
- Synchronization with Palo Alto threat intelligence feeds
Phase 2: Dedicated Security Rule Creation
- Specific blocking rules for each list type
- Top-level positioning in security policy for maximum efficiency
Phase 3: List Separation for Granular Analysis
Contrary to a grouping approach, I deliberately created a distinct rule for each list:
- Advantage: Fine-grained effectiveness analysis via hit counters
- Visibility: Individual performance of each threat intelligence source
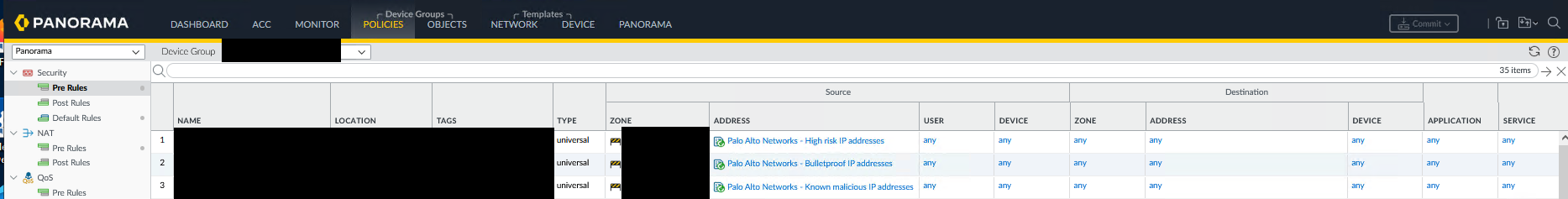 Extract of First Three Security Rules for Malicious IP Filtering
Extract of First Three Security Rules for Malicious IP Filtering
Effectiveness Analysis and Results Obtained
1. Hit Count Analysis Hit counters revealed that “Known-Malicious” and “High-Risk” lists generated the highest number of blocks, confirming their relevance.
2. Security Posture Impact
I conducted a comparative statistical report before/after EDL implementation:
- Significant reduction in medium-severity alerts (sources outside France/Réunion)
- Very strong decrease in medium-severity alerts (international sources) approximately 40%
- Substantial decline in informational alerts
Benefits and Conclusion
This implementation perfectly illustrates how:
- Thorough documentation review
- Exploitation of existing functionalities
- Can significantly improve security posture without additional investment
💡 Lesson Learned: Technical expertise resides not only in implementing new solutions, but also in optimal exploitation of existing capabilities that are often underutilized.
🎓 Learning & Professional Growth
Enterprise-Grade Infrastructure: First hands-on experience configuring and optimizing production security infrastructure for a critical telecommunications operator, requiring careful balance between security effectiveness and service availability requirements.
Advanced NGFW Technologies: Developed expertise in SSL/TLS decryption, CVE monitoring, DoS protection, and threat intelligence integration on enterprise-grade Palo Alto Networks platform.
Operational Experience: Acquired essential skills in enterprise operational frameworks including change management procedures, comprehensive documentation requirements, and multi-team coordination while maintaining stringent security standards.
Project Management & Communication: Led end-to-end project delivery from requirements analysis through production deployment, presenting complex technical concepts to diverse stakeholder audiences, and building fluency in enterprise network and cybersecurity terminology.
Enterprise Methodology: Demonstrated capability to operate effectively within complex multi-vendor environments while delivering measurable security improvements through strategic optimization of existing platform capabilities.
📊 Results & Measurable Impact
Security Posture Enhancement:
- 40% reduction in medium-severity alerts from international threat sources
- Automated EDL built-in integration providing malicious IP blocking without additional licensing costs
- Multi-layer protection deployment featuring CVE monitoring, DoS profiles, and integrated threat intelligence
- Comprehensive documentation in Confluence enabling complete team knowledge transfer and operational continuity
- Threat analysis evolution from manual processes to automated workflows (ThreatDetectionTool implementation)
📎 Resources & Documentation
📄 Download Complete Project Report (PDF)
🔗 Technologies Used: